Customers that purchase both WebLogic Portal (WLP) and AquaLogic Business Process Management (ALBPM) will certainly want them to work together. Specifically, customers want to be able to deploy the ALBPM Workspace user interface as portlets on a WLP portal. This blog explains how to do that, and provides a script to help automate the most tedious steps.
NOTE: this blog entry was originally posted December 17th, 2007 on my previous blogging system (dev2dev.bea.com).
Use Case
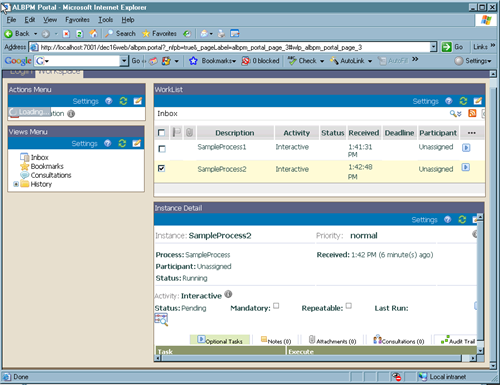
The ALBPM Workspace contains a total of 4 portlets. By default, they deploy in their own pre-built web application. But if you have both ALBPM and WLP in your environment, it would be useful to be able to deploy the portlets into WLP.
The four portlets are:
- Actions Menu: lists the operations the user can perform, like create a new process
- Views Menu: lists the various views available, like process inbox and bookmarks
- Worklist: displays the list as directed by the Views menu, like the list of active processes
- Instance Detail: shows the details of a specific process
A view of the completed Workspace on WLP:
Integration Implementation
Behind the scenes, there are some challenges to this project. First, when the user authenticates with WLP, they shouldn't have to also sign into ALBPM. Fortunately, ALBPM implemented an SSO mechanism in ALBPM 6.0. This can be enabled via a couple of checkboxes during the configuration of ALBPM (more on this later).
Second, the portlets and all supporting file based artifacts need to be brought into the WLP Web Project. While most of this is straightforward, it is an error prone operation. Also, merging in the necessary web.xml entries for the ALBPM workspace into the stock WLP web.xml is tricky. A simple error can create headaches. This part screams for an automated solution.
To make this integration as easy as possible, I have created a distribution that contains movies and an Ant script. The movies will to help guide you through the process. The Ant script removes a lot of tedious steps from the process.
Note: while this integration guide and script are deemed reliable, they are not officially supported. The official documentation is the supported source of information on this integration.
ALBPM 6.0 Workspace for WLP 10
There is official documentation to explain how to integrate the products. But sometimes seeing the integration is the best teacher. Therefore, the distribution that I have created includes a series of movies. Additionally, it contains an overview presentation on the process of integrating the products. Finally, the actual deployment of the ALBPM Workspace onto WLP is scripted via an Ant script that I provide.
I have hosted the files of the distribution in this location:
ALBPM 6.0 Workspace for WLP 10 Download Center
Note: to view the Flash FLV movies you will need an FLV player, such as the free FLVPlayer
ALBPM_for_WLP_slides.zip and ALBPM_for_WLP_slides_movie.zip
Start with these. One zip contains the Powerpoint presentation, the other contains a movie of me talking through the slides. This deck explains what the integration is all about, and the high level steps needed to perform the integration.
ALBPM_for_WLP_movie1.zip, ALBPM_for_WLP_movie2.zip, ALBPM_for_WLP_movie3.zip
These zip files contain detailed walk throughs of various parts of the integration. View these movies in order, and use the Pause button so you can follow along while you perform the integration on your machine.
ALBPM_for_WLP_script.zip
This zip contains the Ant script and associated files that will automate the ALBPM Workspace deployment into WLP. This script does a ton of file copying and also includes some new files (.portlets) to make this a smooth process. While you can do all of this by hand, the script gets the job done quickly and correctly.
Acknowledgements
I didn't complete this project by myself. The ALBPM Development and QA teams (Eduardo, Nico, Mariana, Alex, Mariano, and others) did a lot of work on sorting out the process to get the products integrated. Additionally, some folks from BEA Professional Services (Paddy in particular) helped get this going. THANKS!
Additional Resources
Need more information? Here are some good links to get you started:
- WLP Download - download WebLogic Portal (minimum version 10.0)
- ALBPM Download - download AquaLogic BPM (minimum version 6.0 MP1)
- ALBPM for WLP Official Documentation - official docs for integrating the products
- Alex Toussaint's Blog - ALBPM product manager's blog
- Jesper Joergensen's Blog - ALBPM product marketing blog
- Josh Lannin's Blog - WLP products manager's blog, check out the 5 part WLP futures series

Comments from the original blog:
-
Hi Praveen -
Yes, something with the Apache config is doing strange things with that. We just did a lot of Apache work to speed up the WLP demos, and I am nervous to touch it to sort out the issue. I have found that Firefox, not IE, should be able to download the files fine. Can you try that?
PJL
Posted by: plaird on May 5, 2008 at 11:16 AM
-
Peter, thanks a lot. It seems like a very useful information but I am not able to download using the hyperlinks. Can you pls help me in getting these? my emailID: awasthypr@saic.com Thanks again!!
Posted by: praveenawasthy on May 5, 2008 at 2:15 AM
-
ALBPM 6.0 MP2 Update
I produced the script and movies against ALBPM 6.0 MP1. However, I tested against 6.0 MP2 with success (with one caveat).
The only issue is that there are some JSPs in the ALBPM MP2 workspace that cause the Workshop IDE (WLW) to report build failures (about 45). You will need to disable JSP validation for the WLP web project to get around this.
Project Properties->Validation->uncheck the JSP validator
I have updated the presentation to include this GOTCHA, and will also work with the ALBPM team to discover the root cause.
Thank you Neville for reporting the issue.
PJL
Posted by: plaird on January 8, 2008 at 9:31 AM
-
Kunai -
Sorry about that, I was using an 3rd party file share to host the files. I have rehosted the files on our WLP demo server at wlp.bea.com. I updated the link in the blog too.
Thanks for the note!
Posted by: plaird on January 3, 2008 at 11:35 AM
-
Peter, I'm about to get started on deploying ALBPM Workspace on WLP and I would've loved to have downloaded your slides, movies on the subject. However, it appears that the hyperlinks for these downloads have been disabled. Is there any other way we can exchange this information? Please feel free to send an email at "kunal.r.shah@citi.com" Regards, Kunal R Shah
Posted by: kunalrshah on January 3, 2008 at 11:07 AM